Manually Reset User Password Active Directory
- Active Directory Password Reset Tool
- Active Directory Change User Password
- Reset Password In Active Directory
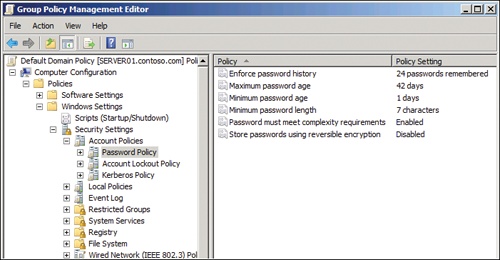
Dec 11, 2017 Force user to change password - Best practice. Not if you're going to manually expire everybody's password at the same time - there is no 'manually expire the password in a couple more days option.' Popular Topics in Active Directory & GPO. Think you've mastered IT? Try the Challenge ». I have been asked to put the following one-time password scenario in place for our (small) Active Directory domain: whenever an administrator has to manually reset a user's password, the password should only be temporary, i.e. The user has to change it at logon, and its validity should be of 24 hours only. The account expiration is stored in the accountExpires attribute of the user's LDAP record. There are two ways (I know) to test the password expiry. Set the maximum password age field of the Default Domain Policy (GPO). Second option is not recommended, but you can try it if you are testing in a virtual machine. Before we forget, let's change our local Administrator user account password from the very insecure non-existent password to something complex. Run the following command: C: net user administrator. Our current task is now to change the default built-in Active Directory Administrator user account password. Resetting Passwords in Active Directory. It's also possible to store Active Directory accounts in Passwordstate, and then reset the password in Active Directory when required - either manually when needed, or on a schedule you choose.
-->Are you having a problem with Azure Active Directory (Azure AD) self-service password reset (SSPR)? The information that follows can help you to get things working again.
Troubleshoot self-service password reset errors that a user might see
| Error | Details | Technical details |
|---|---|---|
| TenantSSPRFlagDisabled = 9 | We’re sorry, you can't reset your password at this time because your administrator has disabled password reset for your organization. There is no further action you can take to resolve this situation. Please contact your admin and ask them to enable this feature. To learn more, see Help, I forgot my Azure AD password. | SSPR_0009: We've detected that password reset has not been enabled by your administrator. Please contact your admin and ask them to enable password reset for your organization. |
| WritebackNotEnabled = 10 | We’re sorry, you can't reset your password at this time because your administrator has not enabled a necessary service for your organization. There is no further action you can take to resolve this situation. Please contact your admin and ask them to check your organization’s configuration. To learn more about this necessary service, see Configuring password writeback. | SSPR_0010: We've detected that password writeback has not been enabled. Please contact your admin and ask them to enable password writeback. |
| SsprNotEnabledInUserPolicy = 11 | We’re sorry, you can't reset your password at this time because your administrator has not configured password reset for your organization. There is no further action you can take to resolve this situation. Contact your admin and ask them to configure password reset. To learn more about password reset configuration, see Quick start: Azure AD self-service password reset. | SSPR_0011: Your organization has not defined a password reset policy. Please contact your admin and ask them to define a password reset policy. |
| UserNotLicensed = 12 | We’re sorry, you can't reset your password at this time because required licenses are missing from your organization. There is no further action you can take to resolve this situation. Please contact your admin and ask them to check your license assignment. To learn more about licensing, see Licensing requirements for Azure AD self-service password reset. | SSPR_0012: Your organization does not have the required licenses necessary to perform password reset. Please contact your admin and ask them to review the license assignments. |
| UserNotMemberOfScopedAccessGroup = 13 | We’re sorry, you can't reset your password at this time because your administrator has not configured your account to use password reset. There is no further action you can take to resolve this situation. Please contact your admin and ask them to configure your account for password reset. To learn more about account configuration for password reset, see Roll out password reset for users. | SSPR_0013: You are not a member of a group enabled for password reset. Contact your admin and request to be added to the group. |
| UserNotProperlyConfigured = 14 | We’re sorry, you can't reset your password at this time because necessary information is missing from your account. There is no further action you can take to resolve this situation. Please contact you admin and ask them to reset your password for you. After you have access to your account again, you need to register the necessary information. To register information, follow the steps in the Register for self-service password reset article. | SSPR_0014: Additional security info is needed to reset your password. To proceed, contact your admin and ask them to reset your password. After you have access to your account, you can register additional security info at https://aka.ms/ssprsetup. Your admin can add additional security info to your account by following the steps in Set and read authentication data for password reset. |
| OnPremisesAdminActionRequired = 29 | We’re sorry, we can't reset your password at this time because of a problem with your organization’s password reset configuration. There is no further action you can take to resolve this situation. Please contact your admin and ask them to investigate. To learn more about the potential problem, see Troubleshoot password writeback. | SSPR_0029: We are unable to reset your password due to an error in your on-premises configuration. Please contact your admin and ask them to investigate. |
| OnPremisesConnectivityError = 30 | We’re sorry, we can't reset your password at this time because of connectivity issues to your organization. There is no action to take right now, but the problem might be resolved if you try again later. If the problem persists, please contact your admin and ask them to investigate. To learn more about connectivity issues, see Troubleshoot password writeback connectivity. | SSPR_0030: We can't reset your password due to a poor connection with your on-premises environment. Contact your admin and ask them to investigate. |
Troubleshoot the password reset configuration in the Azure portal
| Error | Solution |
|---|---|
| I don't see the Password reset section under Azure AD in the Azure portal. | This can happen if you don't have an Azure AD license assigned to the administrator performing the operation. Assign a license to the administrator account in question. You can follow the steps in the Assign, verify, and resolve problems with licenses article. |
| I don't see a particular configuration option. | Many elements of the UI are hidden until they are needed. Try enabling all the options you want to see. |
| I don't see the On-premises integration tab. | This option only becomes visible if you have downloaded Azure AD Connect and have configured password writeback. For more information, see Getting started with Azure AD Connect by using the express settings. |
Troubleshoot password reset reporting
| Error | Solution |
|---|---|
| I don’t see any password management activity types in the Self-Service Password Management audit event category. | This can happen if you don't have an Azure AD license assigned to the administrator performing the operation. You can resolve this problem by assigning a license to the administrator account in question. Follow the steps in the Assign, verify, and resolve problems with licenses article. |
| User registrations show multiple times. | Currently, when a user registers, we log each individual piece of data that's registered as a separate event. If you want to aggregate this data and have greater flexibility in how you can view it, you can download the report and open the data as a pivot table in Excel. |
Troubleshoot the password reset registration portal
| Error | Solution |
|---|---|
| The directory is not enabled for password reset. Your administrator has not enabled you to use this feature. | Switch the Self-service password reset enabled flag to Selected or All and then select Save. |
| The user does not have an Azure AD license assigned. Your administrator has not enabled you to use this feature. | This can happen if you don't have an Azure AD license assigned to the administrator performing the operation. You can resolve this problem by assigning a license to the administrator account in question. Follow the steps in the Assign, verify, and resolve problems with licenses article. |
| There is an error processing the request. | This can be caused by many issues, but generally this error is caused by either a service outage or a configuration issue. If you see this error and it affects your business, contact Microsoft support for additional assistance. |
Troubleshoot the password reset portal
| Error | Solution |
|---|---|
| The directory is not enabled for password reset. | Switch the Self-service password reset enabled flag to Selected or All and then select Save. |
| The user does not have an Azure AD license assigned. | This can happen if you don't have an Azure AD license assigned to the administrator performing the operation. You can resolve this problem if you assign a license to the administrator account in question. Follow the steps in the Assign, verify, and resolve problems with licenses article. |
| The directory is enabled for password reset, but the user has missing or malformed authentication information. | Before proceeding, ensure that user has properly formed contact data on file in the directory. For more information, see Data used by Azure AD self-service password reset. |
| The directory is enabled for password reset, but the user has only one piece of contact data on file when the policy is set to require two verification methods. | Before proceeding, ensure that the user has at least two properly configured contact methods. An example is having both a mobile phone number and an office phone number. |
| The directory is enabled for password reset and the user is properly configured, but the user is unable to be contacted. | This can be the result of a temporary service error or if there is incorrect contact data that we can't properly detect. If the user waits 10 seconds, 'try again' and 'contact your administrator” links appear. If the user selects 'try again,' it retries the call. If the user selects “contact your administrator,” it sends a form email to their administrators requesting a password reset to be performed for that user account. |
| The user never receives the password reset SMS or phone call. | This can be the result of a malformed phone number in the directory. Make sure the phone number is in the format “+ccc xxxyyyzzzzXeeee”. Password reset does not support extensions, even if you specify one in the directory. The extensions are stripped before the call is dispatched. Use a number without an extension or integrate the extension into the phone number in your private branch exchange (PBX). |
| The user never receives the password reset email. | The most common cause for this problem is that the message is rejected by a spam filter. Check your spam, junk, or deleted items folder for the email. Also ensure that you're checking the correct email account for the message. |
| I have set a password reset policy, but when an admin account uses password reset, that policy isn't applied. | Microsoft manages and controls the administrator password reset policy to ensure the highest level of security. |
| The user is prevented from attempting a password reset too many times in a day. | We implement an automatic throttling mechanism to block users from attempting to reset their passwords too many times in a short period of time. Throttling occurs when:
|
| The user sees an error when validating their phone number. | This error occurs when the phone number entered does not match the phone number on file. Make sure the user is entering the complete phone number, including the area and country code, when they attempt to use a phone-based method for password reset. |
| There is an error processing the request. | This can be caused by many issues, but generally this error is caused by either a service outage or a configuration issue. If you see this error and it affects your business, contact Microsoft support for additional assistance. |
| On-premises policy violation | The password does not meet the on-premises Active Directory password policy. |
| Password does not comply fuzzy policy | The password that was used appears in the banned password list and may not be used. |
Troubleshoot password writeback
| Error | Solution |
|---|---|
| The password reset service does not start on-premises. Error 6800 appears in the Azure AD Connect machine’s application event log. After onboarding, federated, pass-through authentication, or password-hash-synchronized users can't reset their passwords. | When password writeback is enabled, the sync engine calls the writeback library to perform the configuration (onboarding) by communicating to the cloud onboarding service. Any errors encountered during onboarding or while starting the Windows Communication Foundation (WCF) endpoint for password writeback results in errors in the event log, on your Azure AD Connect machine. During restart of the Azure AD Sync (ADSync) service, if writeback was configured, the WCF endpoint starts up. But, if the startup of the endpoint fails, we will log event 6800 and let the sync service start up. The presence of this event means that the password writeback endpoint did not start up. Event log details for this event 6800, along with event log entries generate by the PasswordResetService component, indicate why you can't start up the endpoint. Review these event log errors and try to restart the Azure AD Connect if password writeback still isn’t working. If the problem persists, try to disable and then re-enable password writeback. |
| When a user attempts to reset a password or unlock an account with password writeback enabled, the operation fails. In addition, you see an event in the Azure AD Connect event log that contains: “Synchronization Engine returned an error hr=800700CE, message=The filename or extension is too long” after the unlock operation occurs. | Find the Active Directory account for Azure AD Connect and reset the password so that it contains no more than 256 characters. Then open the Synchronization Service from the Start menu. Browse to Connectors and find the Active Directory Connector. Select it and then select Properties. Browse to the Credentials page and enter the new password. Select OK to close the page. |
| At the last step of the Azure AD Connect installation process, you see an error indicating that password writeback couldn't be configured. The Azure AD Connect application event log contains error 32009 with the text “Error getting auth token.” | This error occurs in the following two cases:
|
| The Azure AD Connect machine event log contains error 32002 that is thrown by running PasswordResetService. The error reads: “Error Connecting to ServiceBus. The token provider was unable to provide a security token.” | Your on-premises environment isn't able to connect to the Azure Service Bus endpoint in the cloud. This error is normally caused by a firewall rule blocking an outbound connection to a particular port or web address. See Connectivity prerequisites for more info. After you have updated these rules, reboot the Azure AD Connect machine and password writeback should start working again. |
| After working for some time, federated, pass-through authentication, or password-hash-synchronized users can't reset their passwords. | In some rare cases, the password writeback service can fail to restart when Azure AD Connect has restarted. In these cases, first, check whether password writeback appears to be enabled on-premises. You can check by using either the Azure AD Connect wizard or PowerShell (See the previous HowTos section). If the feature appears to be enabled, try enabling or disabling the feature again either through the UI or PowerShell. If this doesn’t work, try a complete uninstall and reinstall of Azure AD Connect. |
| Federated, pass-through authentication, or password-hash-synchronized users who attempt to reset their passwords see an error after attempting to submit their password. The error indicates that there was a service problem. In addition to this problem, during password reset operations, you might see an error that the management agent was denied access in your on-premises event logs. | If you see these errors in your event log, confirm that the Active Directory Management Agent (ADMA) account that was specified in the wizard at the time of configuration has the necessary permissions for password writeback. After this permission is given, it can take up to one hour for the permissions to trickle down via the sdprop background task on the domain controller (DC). For password reset to work, the permission needs to be stamped on the security descriptor of the user object whose password is being reset. Until this permission shows up on the user object, password reset continues to fail with an access denied message. |
| Federated, pass-through authentication, or password-hash-synchronized users who attempt to reset their passwords, see an error after they submit their password. The error indicates that there was a service problem. In addition to this problem, during password reset operations, you might see an error in your event logs from the Azure AD Connect service indicating an “Object could not be found” error. | This error usually indicates that the sync engine is unable to find either the user object in the Azure AD connector space or the linked metaverse (MV) or Azure AD connector space object. To troubleshoot this problem, make sure that the user is indeed synchronized from on-premises to Azure AD via the current instance of Azure AD Connect and inspect the state of the objects in the connector spaces and MV. Confirm that the Active Directory Certificate Services (AD CS) object is connected to the MV object via the “Microsoft.InfromADUserAccountEnabled.xxx” rule. |
| Federated, pass-through authentication, or password-hash-synchronized users who attempt to reset their passwords see an error after they submit their password. The error indicates that there was a service problem. In addition to this problem, during password reset operations, you might see an error in your event logs from the Azure AD Connect service that indicates that there is a “Multiple matches found” error. | This indicates that the sync engine detected that the MV object is connected to more than one AD CS object via “Microsoft.InfromADUserAccountEnabled.xxx”. This means that the user has an enabled account in more than one forest. This scenario isn't supported for password writeback. |
| Password operations fail with a configuration error. The application event log contains Azure AD Connect error 6329 with the text '0x8023061f (The operation failed because password synchronization is not enabled on this Management Agent)'. | This error occurs if the Azure AD Connect configuration is changed to add a new Active Directory forest (or to remove and readd an existing forest) after the password writeback feature has already been enabled. Password operations for users in these recently added forests fail. To fix the problem, disable and then re-enable the password writeback feature after the forest configuration changes have been completed. |
Password writeback event-log error codes
A best practice when you troubleshoot problems with password writeback is to inspect the application event log, on your Azure AD Connect machine. This event log contains events from two sources of interest for password writeback. The PasswordResetService source describes operations and problems related to the operation of password writeback. The ADSync source describes operations and problems related to setting passwords in your Active Directory environment.
If the source of the event is ADSync
| Code | Name or message | Description |
|---|---|---|
| 6329 | BAIL: MMS(4924) 0x80230619: “A restriction prevents the password from being changed to the current one specified.” | This event occurs when the password writeback service attempts to set a password on your local directory that does not meet the password age, history, complexity, or filtering requirements of the domain. If you have a minimum password age and have recently changed the password within that window of time, you're not able to change the password again until it reaches the specified age in your domain. For testing purposes, the minimum age should be set to 0. If you have password history requirements enabled, then you must select a password that has not been used in the last N times, where N is the password history setting. If you do select a password that has been used in the last N times, then you see a failure in this case. For testing purposes, the password history should be set to 0. If you have password complexity requirements, all of them are enforced when the user attempts to change or reset a password. If you have password filters enabled and a user selects a password that does not meet the filtering criteria, then the reset or change operation fails. |
| 6329 | MMS(3040): admaexport.cpp(2837): The server does not contain the LDAP password policy control. | This problem occurs if LDAP_SERVER_POLICY_HINTS_OID control (1.2.840.113556.1.4.2066) isn't enabled on the DCs. To use the password writeback feature, you must enable the control. To do so, the DCs must be on Windows Server 2008R2 or later. |
| HR 8023042 | Synchronization Engine returned an error hr=80230402, message=An attempt to get an object failed because there are duplicated entries with the same anchor. | This error occurs when the same user ID is enabled in multiple domains. An example is if you're syncing account and resource forests and have the same user ID present and enabled in each forest. This error can also occur if you use a non-unique anchor attribute, like an alias or UPN, and two users share that same anchor attribute. To resolve this problem, ensure that you don't have any duplicated users within your domains and that you use a unique anchor attribute for each user. |
If the source of the event is PasswordResetService
| Code | Name or message | Description |
|---|---|---|
| 31001 | PasswordResetStart | This event indicates that the on-premises service detected a password reset request for a federated, pass-through authentication, or password-hash-synchronized user that originates from the cloud. This event is the first event in every password-reset writeback operation. |
| 31002 | PasswordResetSuccess | This event indicates that a user selected a new password during a password-reset operation. We determined that this password meets corporate password requirements. The password has been successfully written back to the local Active Directory environment. |
| 31003 | PasswordResetFail | This event indicates that a user selected a password and the password arrived successfully to the on-premises environment. But when we attempted to set the password in the local Active Directory environment, a failure occurred. This failure can happen for several reasons:
|
| 31004 | OnboardingEventStart | This event occurs if you enable password writeback with Azure AD Connect and we have started onboarding your organization to the password writeback web service. |
| 31005 | OnboardingEventSuccess | This event indicates that the onboarding process was successful and that the password writeback capability is ready to use. |
| 31006 | ChangePasswordStart | This event indicates that the on-premises service detected a password change request for a federated, pass-through authentication, or password-hash-synchronized user that originates from the cloud. This event is the first event in every password-change writeback operation. |
| 31007 | ChangePasswordSuccess | This event indicates that a user selected a new password during a password change operation, we determined that the password meets corporate password requirements, and that the password has been successfully written back to the local Active Directory environment. |
| 31008 | ChangePasswordFail | This event indicates that a user selected a password and that the password arrived successfully to the on-premises environment, but when we attempted to set the password in the local Active Directory environment, a failure occurred. This failure can happen for several reasons:
|
| 31009 | ResetUserPasswordByAdminStart | The on-premises service detected a password reset request for a federated, pass-through authentication, or password-hash-synchronized user originating from the administrator on behalf of a user. This event is the first event in every password-reset writeback operation that is initiated by an administrator. |
| 31010 | ResetUserPasswordByAdminSuccess | The admin selected a new password during an admin-initiated password-reset operation. We determined that this password meets corporate password requirements. The password has been successfully written back to the local Active Directory environment. |
| 31011 | ResetUserPasswordByAdminFail | The admin selected a password on behalf of a user. The password arrived successfully to the on-premises environment. But when we attempted to set the password in the local Active Directory environment, a failure occurred. This failure can happen for several reasons:
|
| 31012 | OffboardingEventStart | This event occurs if you disable password writeback with Azure AD Connect and indicates that we started offboarding your organization to the password writeback web service. |
| 31013 | OffboardingEventSuccess | This event indicates that the offboarding process was successful and that password writeback capability has been successfully disabled. |
| 31014 | OffboardingEventFail | This event indicates that the offboarding process was not successful. This might be due to a permissions error on the cloud or on-premises administrator account specified during configuration. The error can also occur if you're attempting to use a federated cloud global administrator when disabling password writeback. To fix this problem, check your administrative permissions and ensure that you're not using a federated account while configuring the password writeback capability. |
| 31015 | WriteBackServiceStarted | This event indicates that the password writeback service has started successfully. It is ready to accept password management requests from the cloud. |
| 31016 | WriteBackServiceStopped | This event indicates that the password writeback service has stopped. Any password management requests from the cloud will not be successful. |
| 31017 | AuthTokenSuccess | This event indicates that we successfully retrieved an authorization token for the global admin specified during Azure AD Connect setup to start the offboarding or onboarding process. |
| 31018 | KeyPairCreationSuccess | This event indicates that we successfully created the password encryption key. This key is used to encrypt passwords from the cloud to be sent to your on-premises environment. |
| 32000 | UnknownError | This event indicates an unknown error occurred during a password management operation. Look at the exception text in the event for more details. If you're having problems, try disabling and then re-enabling password writeback. If this does not help, include a copy of your event log along with the tracking ID specified insider to your support engineer. |
| 32001 | ServiceError | This event indicates there was an error connecting to the cloud password reset service. This error generally occurs when the on-premises service was unable to connect to the password-reset web service. |
| 32002 | ServiceBusError | This event indicates there was an error connecting to your tenant’s Service Bus instance. This can happen if you're blocking outbound connections in your on-premises environment. Check your firewall to ensure that you allow connections over TCP 443 and to https://ssprdedicatedsbprodncu.servicebus.windows.net, and then try again. If you're still having problems, try disabling and then re-enabling password writeback. |
| 32003 | InPutValidationError | This event indicates that the input passed to our web service API was invalid. Try the operation again. |
| 32004 | DecryptionError | This event indicates that there was an error decrypting the password that arrived from the cloud. This might be due to a decryption key mismatch between the cloud service and your on-premises environment. To resolve this problem, disable and then re-enable password writeback in your on-premises environment. |
| 32005 | ConfigurationError | During onboarding, we save tenant-specific information in a configuration file in your on-premises environment. This event indicates that there was an error saving this file or that when the service was started, there was an error reading the file. To fix this problem, try disabling and then re-enabling password writeback to force a rewrite of the configuration file. |
| 32007 | OnBoardingConfigUpdateError | During onboarding, we send data from the cloud to the on-premises password-reset service. That data is then written to an in-memory file before it is sent to the sync service to be stored securely on disk. This event indicates that there is a problem with writing or updating that data in memory. To fix this problem, try disabling and then re-enabling password writeback to force a rewrite of this configuration file. |
| 32008 | ValidationError | This event indicates we received an invalid response from the password-reset web service. To fix this problem, try disabling and then re-enabling password writeback. |
| 32009 | AuthTokenError | This event indicates that we couldn't get an authorization token for the global administrator account specified during Azure AD Connect setup. This error can be caused by a bad username or password specified for the global admin account. This error can also occur if the global admin account specified is federated. To fix this problem, rerun the configuration with the correct username and password and ensure that the administrator is a managed (cloud-only or password-synchronized) account. |
| 32010 | CryptoError | This event indicates there was an error generating the password encryption key or decrypting a password that arrives from the cloud service. This error likely indicates a problem with your environment. Look at the details of your event log to learn more about how to resolve this problem. You can also try disabling and then re-enabling the password writeback service. |
| 32011 | OnBoardingServiceError | This event indicates that the on-premises service couldn't properly communicate with the password-reset web service to initiate the onboarding process. This can happen as a result of a firewall rule or if there is a problem getting an authentication token for your tenant. To fix this problem, ensure that you're not blocking outbound connections over TCP 443 and TCP 9350-9354 or to https://ssprdedicatedsbprodncu.servicebus.windows.net. Also ensure that the Azure AD admin account you're using to onboard isn't federated. |
| 32013 | OffBoardingError | This event indicates that the on-premises service couldn't properly communicate with the password-reset web service to initiate the offboarding process. This can happen as a result of a firewall rule or if there is a problem getting an authorization token for your tenant. To fix this problem, ensure that you're not blocking outbound connections over 443 or to https://ssprdedicatedsbprodncu.servicebus.windows.net, and that the Azure Active Directory admin account you're using to offboard isn't federated. |
| 32014 | ServiceBusWarning | This event indicates that we had to retry to connect to your tenant’s Service Bus instance. Under normal conditions, this should not be a concern, but if you see this event many times, consider checking your network connection to Service Bus, especially if it’s a high-latency or low-bandwidth connection. |
| 32015 | ReportServiceHealthError | In order to monitor the health of your password writeback service, we send heartbeat data to our password-reset web service every five minutes. This event indicates that there was an error when sending this health information back to the cloud web service. This health information does not include an object identifiable information (OII) or personally identifiable information (PII) data, and is purely a heartbeat and basic service statistics so that we can provide service status information in the cloud. |
| 33001 | ADUnKnownError | This event indicates that there was an unknown error returned by Active Directory. Check the Azure AD Connect server event log for events from the ADSync source for more information. |
| 33002 | ADUserNotFoundError | This event indicates that the user who is trying to reset or change a password was not found in the on-premises directory. This error can occur when the user has been deleted on-premises but not in the cloud. This error can also occur if there is a problem with sync. Check your sync logs and the last few sync run details for more information. |
| 33003 | ADMutliMatchError | When a password reset or change request originates from the cloud, we use the cloud anchor specified during the setup process of Azure AD Connect to determine how to link that request back to a user in your on-premises environment. This event indicates that we found two users in your on-premises directory with the same cloud anchor attribute. Check your sync logs and the last few sync run details for more information. |
| 33004 | ADPermissionsError | This event indicates that the Active Directory Management Agent (ADMA) service account does not have the appropriate permissions on the account in question to set a new password. Ensure that the ADMA account in the user’s forest has reset and change password permissions on all objects in the forest. For more information on how to set the permissions, see Step 4: Set up the appropriate Active Directory permissions. This error could also occur when the user's attribute AdminCount is set to 1. |
| 33005 | ADUserAccountDisabled | This event indicates that we attempted to reset or change a password for an account that was disabled on-premises. Enable the account and try the operation again. |
| 33006 | ADUserAccountLockedOut | This event indicates that we attempted to reset or change a password for an account that was locked out on-premises. Lockouts can occur when a user has tried a change or reset password operation too many times in a short period. Unlock the account and try the operation again. |
| 33007 | ADUserIncorrectPassword | This event indicates that the user specified an incorrect current password when performing a password change operation. Specify the correct current password and try again. |
| 33008 | ADPasswordPolicyError | This event occurs when the password writeback service attempts to set a password on your local directory that does not meet the password age, history, complexity, or filtering requirements of the domain. If you have a minimum password age and have recently changed the password within that window of time, you're not able to change the password again until it reaches the specified age in your domain. For testing purposes, the minimum age should be set to 0. If you have password history requirements enabled, then you must select a password that has not been used in the last N times, where N is the password history setting. If you do select a password that has been used in the last N times, then you see a failure in this case. For testing purposes, the password history should be set to 0. If you have password complexity requirements, all of them are enforced when the user attempts to change or reset a password. If you have password filters enabled and a user selects a password that does not meet the filtering criteria, then the reset or change operation fails. |
| 33009 | ADConfigurationError | This event indicates there was a problem writing a password back to your on-premises directory because of a configuration issue with Active Directory. Check the Azure AD Connect machine’s application event log for messages from the ADSync service for more information on which error occurred. |
Troubleshoot password writeback connectivity
If you're experiencing service interruptions with the password writeback component of Azure AD Connect, here are some quick steps you can take to resolve this problem:
In general, to recover your service in the most rapid manner, we recommend that you execute these steps in the order discussed previously.
Confirm network connectivity
The most common point of failure is that firewall and or proxy ports and idle timeouts are incorrectly configured.
For Azure AD Connect version 1.1.443.0 and above, you need outbound HTTPS access to the following:
- *.passwordreset.microsoftonline.com
- *.servicebus.windows.net
For more granularity, reference the updated list of Microsoft Azure Datacenter IP Ranges updated every Wednesday and put into effect the next Monday.
For more information, review the connectivity prerequisites in the Prerequisites for Azure AD Connect article.
Note
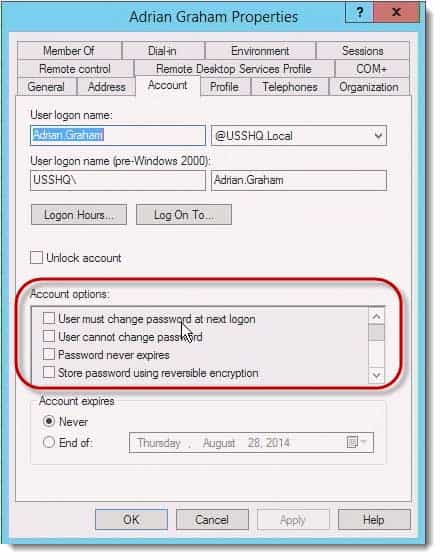
SSPR can also fail if the 'Password never expires' or 'User cannot change password' settings are configured on the account in AD DS on-premises.
Restart the Azure AD Connect Sync service
To resolve connectivity problems or other transient problems with the service, restart the Azure AD Connect Sync service:
As an administrator, select Start on the server running Azure AD Connect.
Enter services.msc in the search field and select Enter.
Look for the Microsoft Azure AD Sync entry.
Right-click the service entry, select Restart, and then wait for the operation to finish.
These steps re-establish your connection with the cloud service and resolve any interruptions you might be experiencing. If restarting the ADSync service does not resolve your problem, we recommend that you try to disable and then re-enable the password writeback feature.
Disable and re-enable the password writeback feature
To resolve connectivity issues, disable and then re-enable the password writeback feature:
- As an administrator, open the Azure AD Connect Configuration wizard.
- In Connect to Azure AD, enter your Azure AD global admin credentials.
- In Connect to AD DS, enter your AD Domain Services admin credentials.
- In Uniquely identifying your users, select the Next button.
- In Optional features, clear the Password writeback check box.
- Select Next through the remaining dialog pages without changing anything until you get to the Ready to configure page.
- Ensure that the Ready to configure page shows the Password writeback option as disabled and then select the green Configure button to commit your changes.
- In Finished, clear the Synchronize now option, and then select Finish to close the wizard.
- Reopen the Azure AD Connect Configuration wizard.
- Repeat steps 2-8, except ensure you select the Password writeback option on the Optional features page to re-enable the service.
These steps re-establish your connection with our cloud service and resolve any interruptions you might be experiencing.
If disabling and then re-enabling the password writeback feature does not resolve your problem, we recommend that you reinstall Azure AD Connect.
Install the latest Azure AD Connect release
Reinstalling Azure AD Connect can resolve configuration and connectivity issues between our cloud services and your local Active Directory environment.
We recommend that you perform this step only after you attempt the first two steps previously described.
Warning
If you have customized the out-of-the-box sync rules, back them up before proceeding with upgrade and then manually redeploy them after you're finished.
- Download the latest version of Azure AD Connect from the Microsoft Download Center.
- Because you have already installed Azure AD Connect, you need to perform an in-place upgrade to update your Azure AD Connect installation to the latest version.
- Execute the downloaded package and follow the on-screen instructions to update your Azure AD Connect machine.
The previous steps should re-establish your connection with our cloud service and resolve any interruptions you might be experiencing.
If installing the latest version of the Azure AD Connect server does not resolve your problem, we recommend that you try disabling and then re-enabling password writeback as a final step after you install the latest release.
Verify that Azure AD Connect has the required permission for password writeback
Azure AD Connect requires Active Directory Reset password permission to perform password writeback. To find out if Azure AD Connect has the required permission for a given on-premises Active Directory user account, you can use the Windows Effective Permission feature:
Sign in to the Azure AD Connect server and start the Synchronization Service Manager by selecting Start > Synchronization Service.
Under the Connectors tab, select the on-premises Active Directory Domain Services connector, and then select Properties.
In the pop-up window, select Connect to Active Directory Forest and make note of the User name property. This property is the AD DS account used by Azure AD Connect to perform directory synchronization. For Azure AD Connect to perform password writeback, the AD DS account must have reset password permission.
Sign in to an on-premises domain controller and start the Active Directory Users and Computers application.
Select View and make sure the Advanced Features option is enabled.
Look for the Active Directory user account you want to verify. Right-click the account name and select Properties.
In the pop-up window, go to the Security tab and select Advanced.
In the Advanced Security Settings for Administrator pop-up window, go to the Effective Access tab.
This instrument is easy-to-use, and sources and measures 12 thermocouple and seven RTD types, plus volts and ohms.Additionally, this tool as well handles high-speed pulsed RTD circuits and provides loop power. Fluke 724 OffersTest and calibrate all temperature sensors and transmitters in your plant with only this temperature calibrator. Fluke temp calibrator.
Select Select a user, select the AD DS account used by Azure AD Connect (see step 3), and then select View effective access.
Scroll down and look for Reset password. If the entry has a check mark, the AD DS account has permission to reset the password of the selected Active Directory user account.
Azure AD forums
If you have a general question about Azure AD and self-service password reset, you can ask the community for assistance on the Azure AD forums. Members of the community include engineers, product managers, MVPs, and fellow IT professionals.
Contact Microsoft support
If you can't find the answer to a problem, our support teams are always available to assist you further.
To properly assist you, we ask that you provide as much detail as possible when opening a case. These details include:
General description of the error: What is the error? What was the behavior that was noticed? How can we reproduce the error? Provide as much detail as possible.
Page: What page were you on when you noticed the error? Include the URL if you're able to and a screenshot of the page.
Support code: What was the support code that was generated when the user saw the error?
- To find this code, reproduce the error, then select the Support code link at the bottom of the screen and send the support engineer the GUID that results.
- If you're on a page without a support code at the bottom, select F12 and search for the SID and CID and send those two results to the support engineer.
Date, time, and time zone: Include the precise date and time with the time zone that the error occurred.
User ID: Who was the user who saw the error? An example is user@contoso.com.
- Is this a federated user?
- Is this a pass-through authentication user?
- Is this a password-hash-synchronized user?
- Is this a cloud-only user?
Licensing: Does the user have an Azure AD license assigned?
Application event log: If you're using password writeback and the error is in your on-premises infrastructure, include a zipped copy of your application event log from the Azure AD Connect server.
Next steps
The following articles provide additional information about password reset through Azure AD:
-->
Active Directory Password Reset Tool
If you forgot your password, never got one from your company support, or have been locked out of your account, you can use your security info and your mobile device to reset your password.
Note
If you know your password and just want to change it, you can go to the Change your password steps in this article.
If you're trying to get back into a personal account like Xbox, hotmail.com, or outlook.com, try the suggestions in the When you can't sign in to your Microsoft account article.
How to reset or unlock your password for a work or school account
If you can't access your Azure Active Directory (Azure AD) account, it could be because either:
Your password isn't working and you want to reset it, or
You know your password, but your account is locked out and you need to unlock it.
To reset your password and get back into your account
In the Enter password screen, select Forgot my password.
In the Get back into your account screen, type your work or school User ID (for example, your email address), prove you aren't a robot by entering the characters you see on the screen, and then select Next.
Note
If your administrator hasn't turned on the ability for you to reset your own password, you'll see a Contact your administrator link instead of the Get back into your account screen. This link lets you contact your administrator about resetting your password, through either email or a web portal.
Choose one of the following methods to verify your identity and change your password. Depending on how your administrator has set up your organization, you might need to go through this process a second time, adding info for a second verification step.
Note
Depending on how your administrator has set up your organization, some of these verification options might not be available. You must have previously set up your mobile device for verification using at least one of these methods.
Additionally, your new password might need to meet certain strength requirements. Strong passwords typically have 8 to 16 characters, including upper and lowercase characters, at least one number, and at least one special character.
Reset your password using an email address. Sends an email to the email address you previously set up in two-step verification or security info. If your administrator has turned on the security info experience, you can find more info about setting up an email address in the Set up security info to use email (preview) article. If you're not yet using security info, you can find more info about setting up an email address in the Set up my account for two-step verification article.
Select Email my alternate email, and then select Email.
Type the verification code from the email into the box, and then select Next.
Type and confirm your new password, and then select Finish.
Reset your password using a text message. Sends a text message to the phone number you previously set up in security info. If your administrator has turned on the security info experience, you can find more info about setting up text messaging in the Set up security info to use text messaging (preview) article. If you're not yet using security info, you can find more info about setting up text messaging in the Set up my account for two-step verification article.
Select Text my mobile phone, type your phone number, and then select Text.
Type the verification code from the text message into the box, and then select Next.
Type and confirm your new password, and then select Finish.
Reset your password using a phone number. Sends a text message to the phone number you previously set up in security info. If your administrator has turned on the security info experience, you can find more info about setting up a phone number in the Set up security info to use a phone call (preview) article. If you're not yet using security info, you can find more info about setting up a phone number in the Set up my account for two-step verification article.
Select Call my mobile phone, type your phone number, and then select Call.
Answer the phone call and follow the instructions to verify your identity, and then select Next.
Type and confirm your new password, and then select Finish.
Reset your password using security questions. Shows you the list of security questions you set up in security info. If your administrator has turned on the security info experience, you can find more info about setting up your security questions in the Set up security info to use pre-defined security questions (preview) article. If you're not yet using security info, you can find more info about setting up security questions in the Set up my account for two-step verification article.
Select Answer my security questions, answer the questions, and then select Next.
Type and confirm your new password, and then select Finish.
Reset your password using a notification from your authenticator app. Sends an approval notification to the authenticator app. If your administrator has turned on the security info experience, you can find more info about setting up an authenticator app to send a notification in the Set up security info to use an authentication app (preview) article. If you're not yet using security info, you can find more info about setting up an authenticator app to send a notification in the Set up my account for two-step verification article.
Select Approve a notification on my authenticator app, and then select Send Notification.
Approve the sign-in from your authenticator app.
Type and confirm your new password, and then select Finish.
Reset your password using a code from your authenticator app. Accepts a random code provided by your authentication app. If your administrator has turned on the security info experience, you can find more info about setting up an authenticator app to provide a code in the Set up security info to use an authentication app (preview) article. If you're not yet using security info, you can find more info about setting up an authenticator app to provide a code in the Set up my account for two-step verification article.
Select Enter a code from my authenticator app, and then select Send Notification.
Open your authenticator app, type the verification code for your account into the box, and then select Next.
Type and confirm your new password, and then select Finish.
View and Download Bose Acoustimass 10 Series III owner's manual online. Home entertainment speaker system. Acoustimass 10 Series III Home Cinema speakers pdf manual download. Also for: Acoustimass 6 iii series, Am 6 iii, Acoustimass 6 series iii. Bose acoustimass 10 series iii user manual. We appreciate your choice of the Bose ® Acoustimass ® 6 Series III or Acoustimass 10 Series III home entertainment speaker system. Bose Virtually Invisible ® speaker technology allows you to enjoy lifelike home performances from the very latest surround-sound encoded movies, CDs, and television shows, without a room full of speakers. Bose Acoustimass 10 Series III Pdf User Manuals. View online or download Bose Acoustimass 10 Series III Owner's Manual. Discover product support for your Acoustimass 10 Series III home theater speaker system. Learn how to operate your product through helpful tips, technical support information and product manuals. Purchase parts and accessories.
After you get the message saying that your password has been reset, you can sign in to your account using your new password.
If you still can't access your account, you should contact your organization's administrator for more help.
After resetting your password, you might get a confirmation email that comes from an account like, 'Microsoft on behalf of <your_organization>.' If you get a similar email, but you didn't recently reset your password, you must contact your organization's administrator immediately.
How to change your password
If you just want to change your password, you can do it through the Office 365 portal, the Azure Access Panel, or the Windows 10 sign-in page.
To change your password using the Office 365 portal
Use this method if you typically access your apps through the Office portal:
Sign in to your Office 365 account, using your existing password.
Select your profile on the upper-right side, and then select View account.
Select Security & privacy > Password.
Type your old password, create and confirm your new password, and then select Submit.
To change your password from the Azure Access Panel
Use this method if you typically access your apps from the Azure Access Panel (MyApps):
Sign in to the Azure Access Panel, using your existing password.
Select your profile on the upper-right side, and then select Profile.
Select Change password.
Type your old password, create and confirm your new password, and then select Submit.
To change your password at Windows sign-in
If your administrator turned on the functionality, you can see a link to Reset password on your Windows 7, Windows 8, Windows 8.1, or Windows 10 sign-in screen.
Select the Reset password link to start the password reset process without having to use the normal web-based experience.
Confirm your user ID and select Next.
Select and confirm a contact method for verification. If necessary, choose a second verification option that's different from your previous one, filling in the necessary info.
On the Create a new password page, type and confirm your new password, and then select Next.
Strong passwords typically have 8 to 16 characters, including upper and lowercase characters, at least one number, and at least one special character.
After you get the message saying that your password has been reset, you can select Finish.
If you still can't access your account, you should contact your organization's administrator for more help.
Common problems and their solutions
Active Directory Change User Password
Here are some common error cases and their solutions:
| Problem | Description | Solution |
|---|---|---|
| When I try to change my password, I get an error. | Your password has a word, phrase, or pattern that makes your password easily guessable. | Try again using a stronger password. |
| After I enter my User ID, I go to a page that says, 'Please contact your administrator.' | Microsoft has determined that your user account password is managed by your administrator in an on-premises environment. As a result, you can't reset your password from the 'Can't access your account' link. | Contact your administrator for more help. |
| After I enter my User ID, I get an error that says, 'Your account is not enabled for password reset.' | Your administrator hasn't set up your account so you can reset your own password. | Your administrator hasn't turned on password reset for your organization from the 'Can't access your account' link, or hasn't licensed you to use the feature. To reset your password, you must select the 'contact an administrator link' to send an email to your company's administrator, and let them know you want to reset your password. |
| After I enter my User ID, I get an error that says, 'We couldn't verify your account.' | The sign-in process was unable to verify your account info. | There are two reasons you could be seeing this message. 1. Your administrator turned on password reset for your organization, but you haven't registered to use the service. To register for password reset, see one of the following articles, based on your verification method: Set up security info to use an authenticator app (preview), Set up security info to use a phone call (preview), Set up security info to use text messaging (preview), Set up security info to use email (preview), or Set up security info to use security questions (preview). 2. Your administrator hasn't turned on password reset for your organization. In this situation, you must select the 'contact an administrator link' to send an email to your administrator, asking to reset your password. |
Next steps
Reset Password In Active Directory
Learn about security info in the Security info (preview) overview article.
Learn about two-step verification in the Two-step verification overview article.
Reset your password if you've lost or forgotten it, from the Password reset portal
Get troubleshooting tips and help for sign-in problems in the Can't sign in to your Microsoft account article.